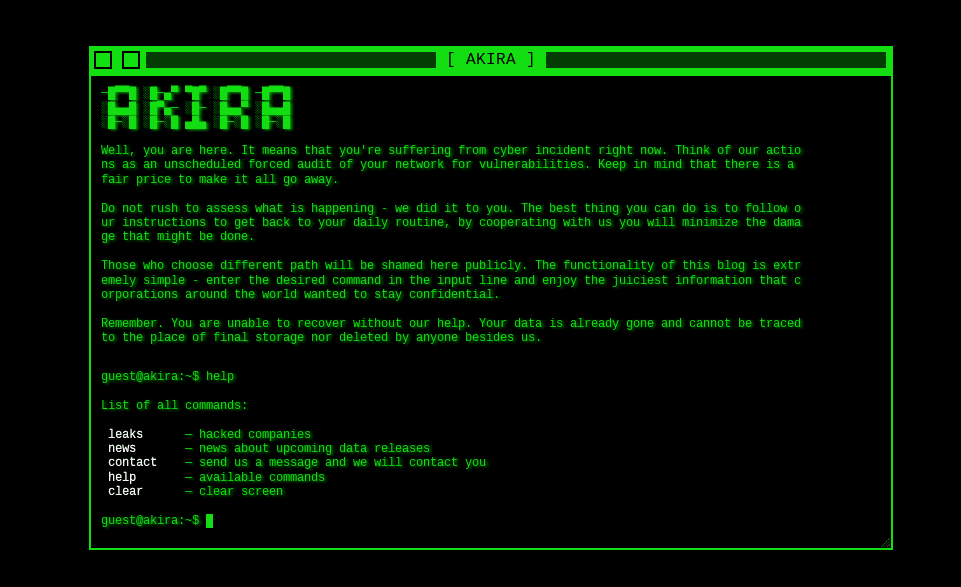
Traditional ransomware groups might hide in a network for weeks, but Akira is a sprint. It can move from a compromised VPN gateway to full-scale encryption in as little as 120 minutes. For organizations like Stanford University or Nissan Australia, Akira became a coordinated strike against their ability to recover.
In July 2025, Akira began weaponizing critical SonicWall SSL VPN vulnerabilities to bypass MFA, often achieving total network compromise in under two hours. Our SOC engineers recently neutralized an attack of this type, identifying the unauthorized entry point in real-time and evicting the hackers before they could execute their wiper scripts on the backup servers. Speaking from experience, we developed this Akira Playbook to translate our forensic findings into a tactical roadmap.
Lesson 1: Your SOC should monitor day and night
Akira’s primary weapon is the “speedrun” approach, utilizing a 2-hour window that exploits the gap between alert triggering and a human analyst taking action. If your SOC is still operating on a “next business day,” you are gonna get hit.
Security Tip:
Monitor for rapid lateral movement via RDP (Event ID X, Logon Type Y) and the sudden deployment of dual-use tools like AnyDesk or Ngrok in non-admin profiles.
Don’t let a retro screen be your last warning
Download our Akira Playbook to master the 120-minute response cycle.
Lesson 2: Veeam is a target
One of Akira’s first objectives after gaining administrative access is to locate and wipe Veeam backup repositories. They use custom PowerShell scripts to delete Volume Shadow Copies and disable security software, ensuring that by the time the ransom note appears, your “Plan B” has already been erased.
Security Tip:
Use a locked backup system where your data is frozen. If your backup service account has enough permissions to delete its own archives, so does Akira.
Lesson 3: Your VPN is the welcome mat
Akira just needs an unpatched door to enter. The hacker group consistently exploits vulnerabilities in Cisco ASA/FTD and SonicWall VPNs, specifically targeting accounts without MFA or using legacy single-factor authentication.
Security Tip:
Patching is the bare minimum. You must enforce phishing-resistant MFA and conduct regular audits of VPN session logs for anomalous IPs originating from TOR exit nodes.
Lesson 4: The no-reboot rule
When the first .akira extension appears, the instinct for many IT managers is to pull the plug. However, Akira often leaves traces of encryption keys and C2 artifacts in the system’s RAM. Powering down the machine destroys this evidence and removes any chance of retrieving decryption keys through memory forensics.
Security Tip:
Use tools like Magnet RAM Capture to preserve the state of the IIS worker processes (w3wp.exe) before they are isolated.
Lesson 5: Living off the fat of your land
Why work hard if you can use the victim’s own legitimate administrative tools (RClone for exfiltration, AnyDesk for persistence, and PowerShell for execution) to blend into daily traffic? That’s Akira’s motto. To a basic EDR, an admin using AnyDesk looks normal. To a seasoned SOC engineer, it looks like a breach in progress.
How UnderDefense Helps
UnderDefense doesn’t just watch for alerts — we hunt for the ambiguous signals that Akira uses as cover.
- 24/7 and fast response
We operate within Akira’s 120-minute window, providing immediate containment and eviction.
- Precision forensics
Our team specializes in memory-centric analysis to identify the initial entry point (like a bypassed VPN) and recover critical data.
- Strategic hardening
We move beyond “cleanup” to ensure your Veeam repositories and gateways are battle-hardened against future iterations of the threat.
Need help now?
UnderDefense’s Security Team is available 24/7. Immediate triage, containment, and forensic assistance.
1. Can Akira bypass MFA?
Yes, Akira often uses MFA fatigue (spamming push notifications) or exploits legacy VPN protocols that don’t support modern MFA.
2. Why does Akira target ESXi servers?
By encrypting the hypervisor, Akira ransomware can lock dozens of virtual machines simultaneously, maximizing the damage with minimal effort.
3. Should I pay the ransom if Akira has my data?
No, payment is not a guarantee of data deletion. We recommend contacting a seasoned cybersecurity vendor who can help you remove the ransomware and establish improved protection for the future.
The post Vintage Outside, Savage Inside: Lessons from the Akira Ransomware Blitz appeared first on UnderDefense.